This post is about the GCP VPC Firewall setup challenge where you can learn how to setup incoming (Ingress) and Outgoing (Egress) firewall within the VPC network.
This setup also uses the following:
- Service Accounts
- Instance Template
- Instance Groups
- VPC
Challenge Build
- Two-tier setup:
- Frontend
- Accept incoming request from internet (able to ping these instances)
- Can connect outbound to backend and internet
- Backend
- Should NOT accept incoming request from the internet
- ONLY accept incoming from frontend or other backend
- Does not connect to the internet (no outbound anywhere excpept other backend)
- Frontend
- Auto-scaled across 2+ zones
- Use ICMP ping to represent allowed firewall traffic
- Real world usage use: 80, 443, 3306
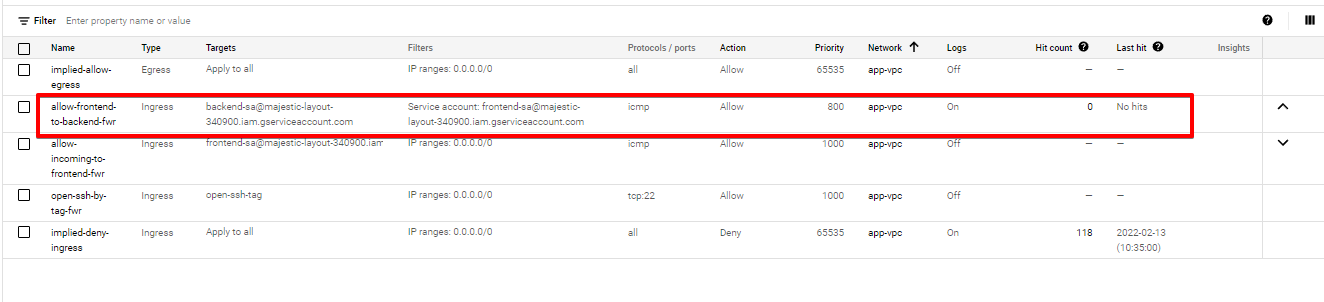
- All firewall rules based on service accounts (except open-ssh-tag – don’t add this TAG!)
Desired results:
Tips:
- Clean up!
- Disable autoscalling / 0 instances
- Or delete project
Setup
Roles
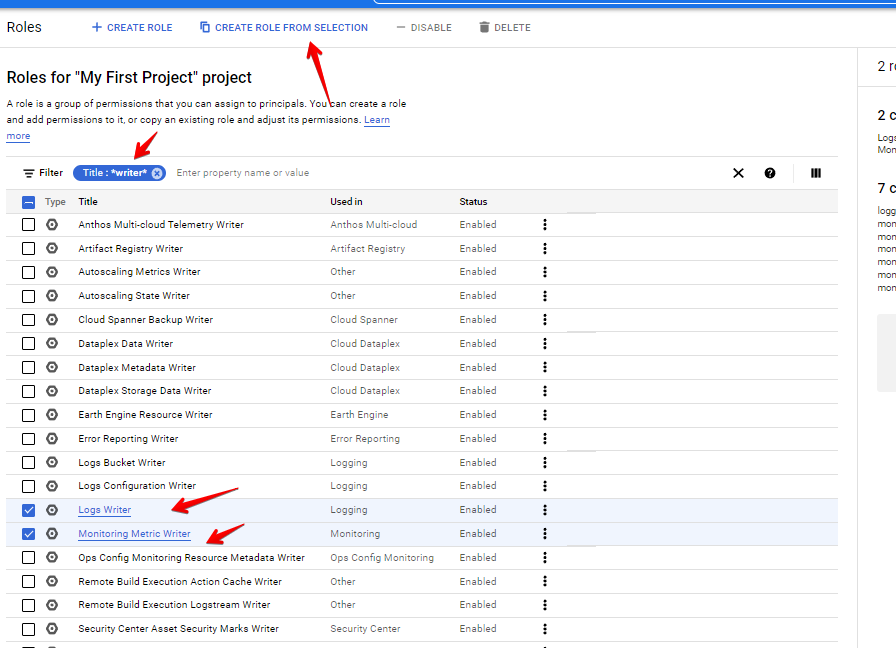
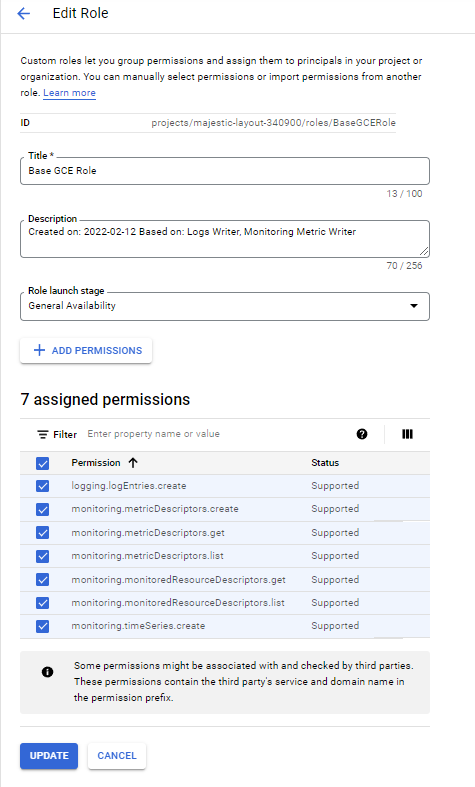
Service accounts:
- backend-sa – Screenshots example upon creation
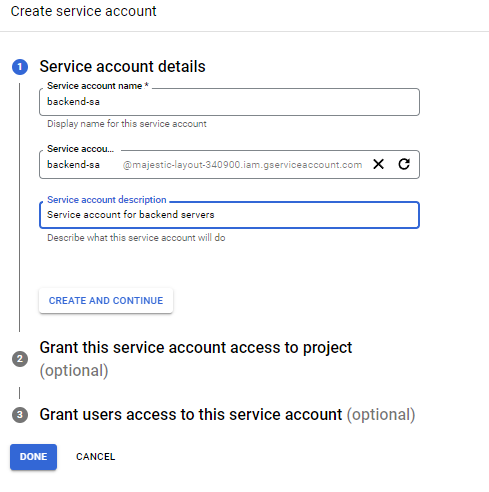
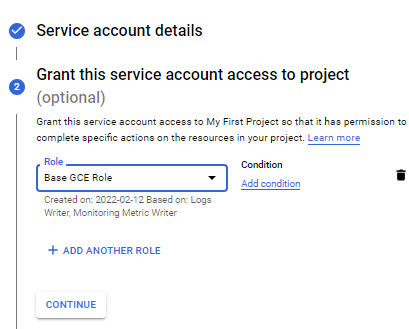
- frontend-sa – The same setup as above

VPC
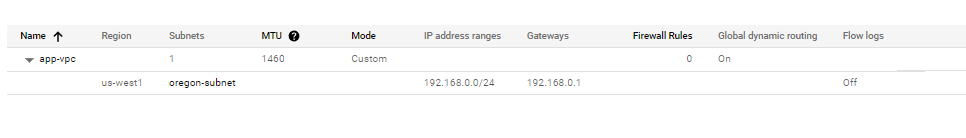
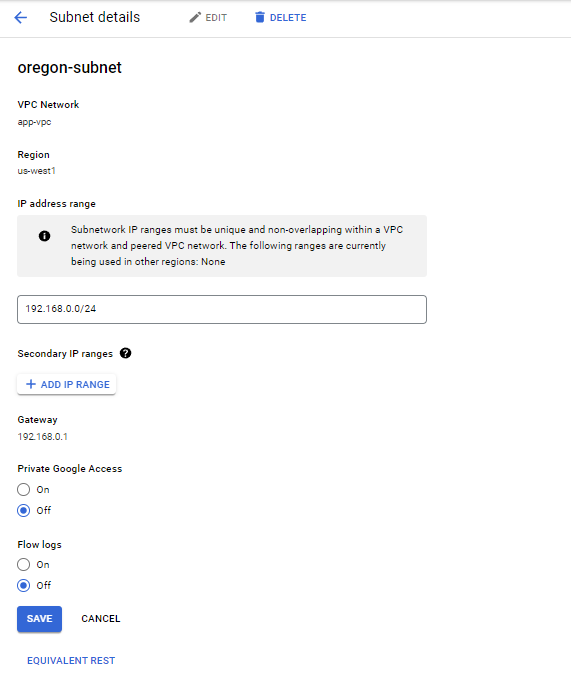
Instance template
Backend instance template example creation
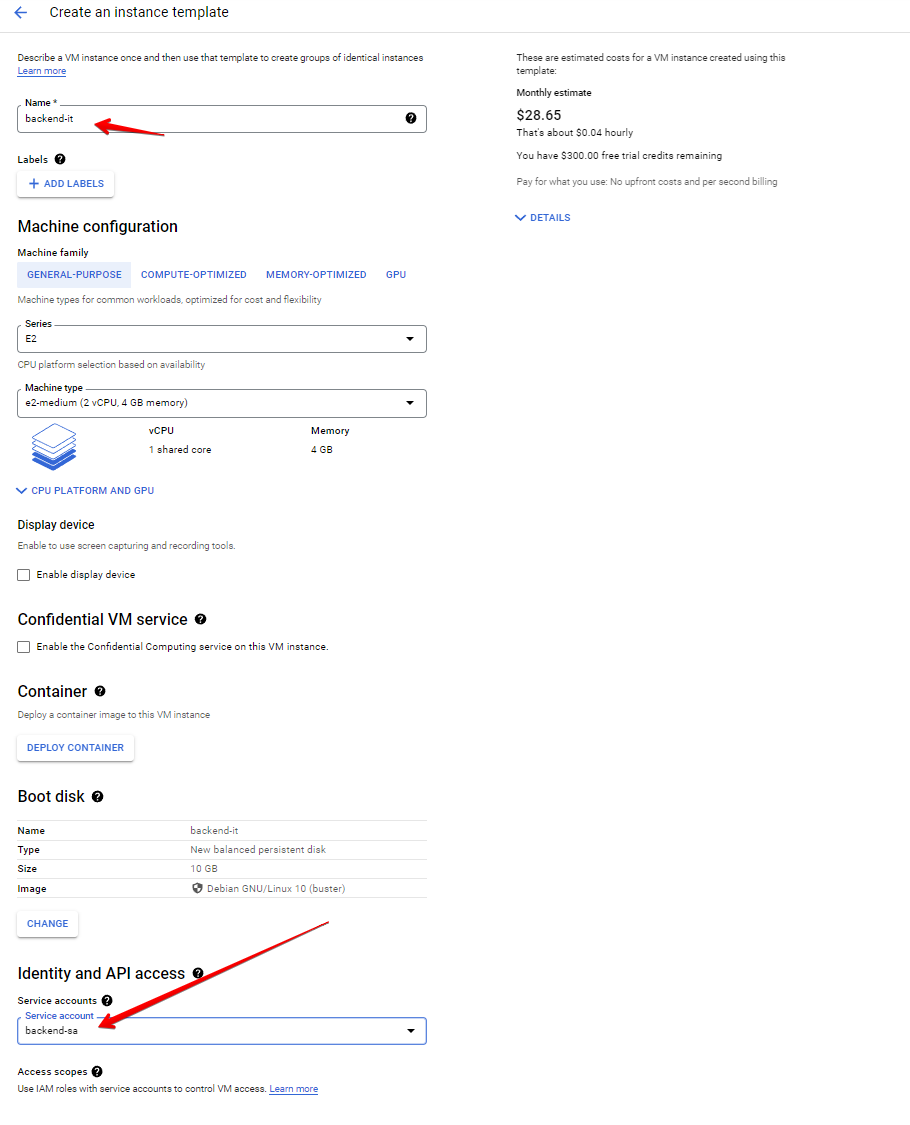

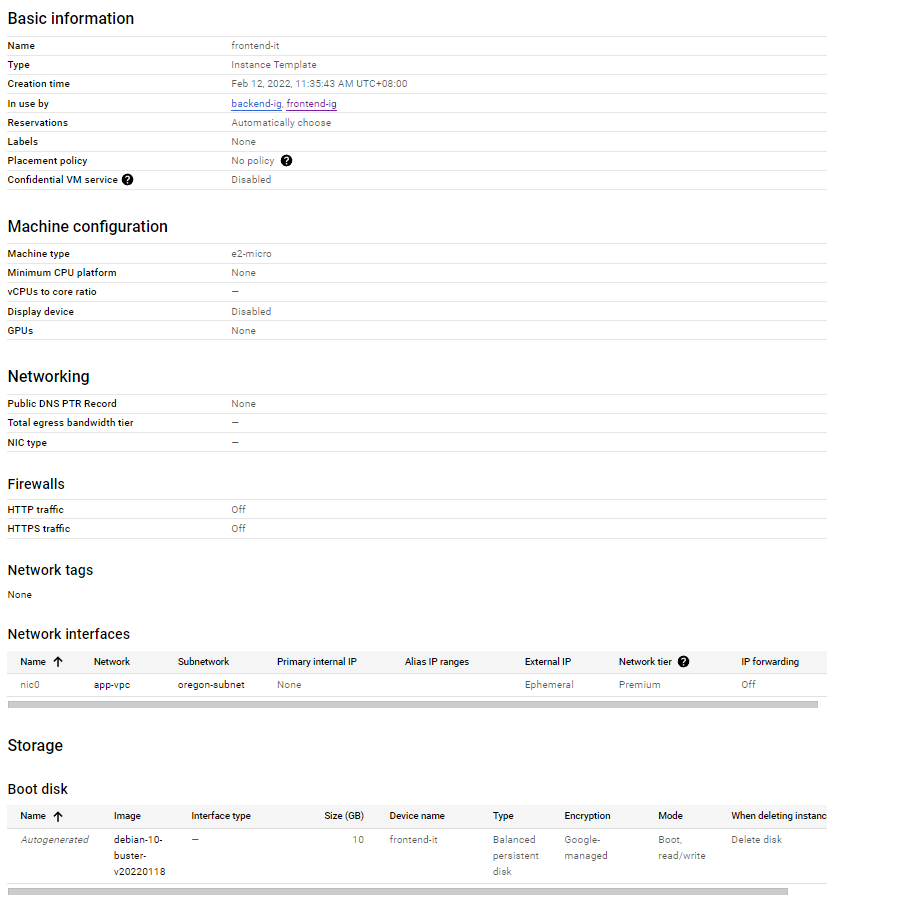
Instance group from instance template


Results:
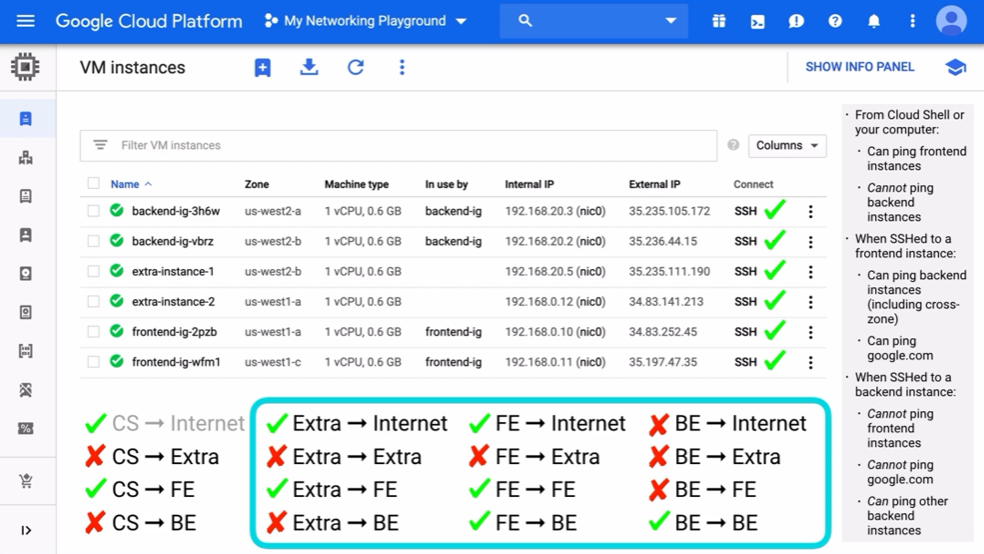
Validation:
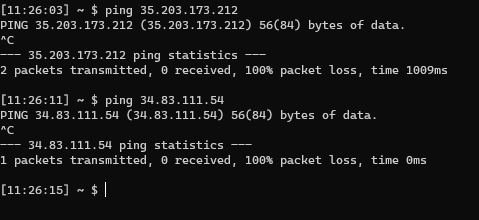
- From Cloud Shell or your computer:
- You can ping frontend instances

- From Cloud Shell or your computer:
- Should not be able to ping backend instances
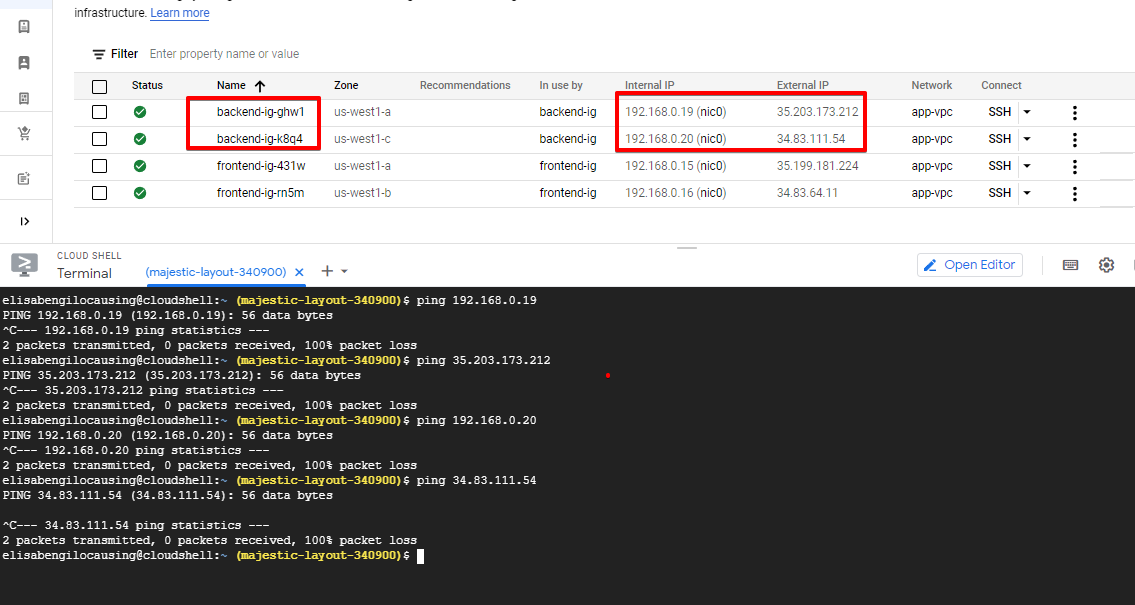
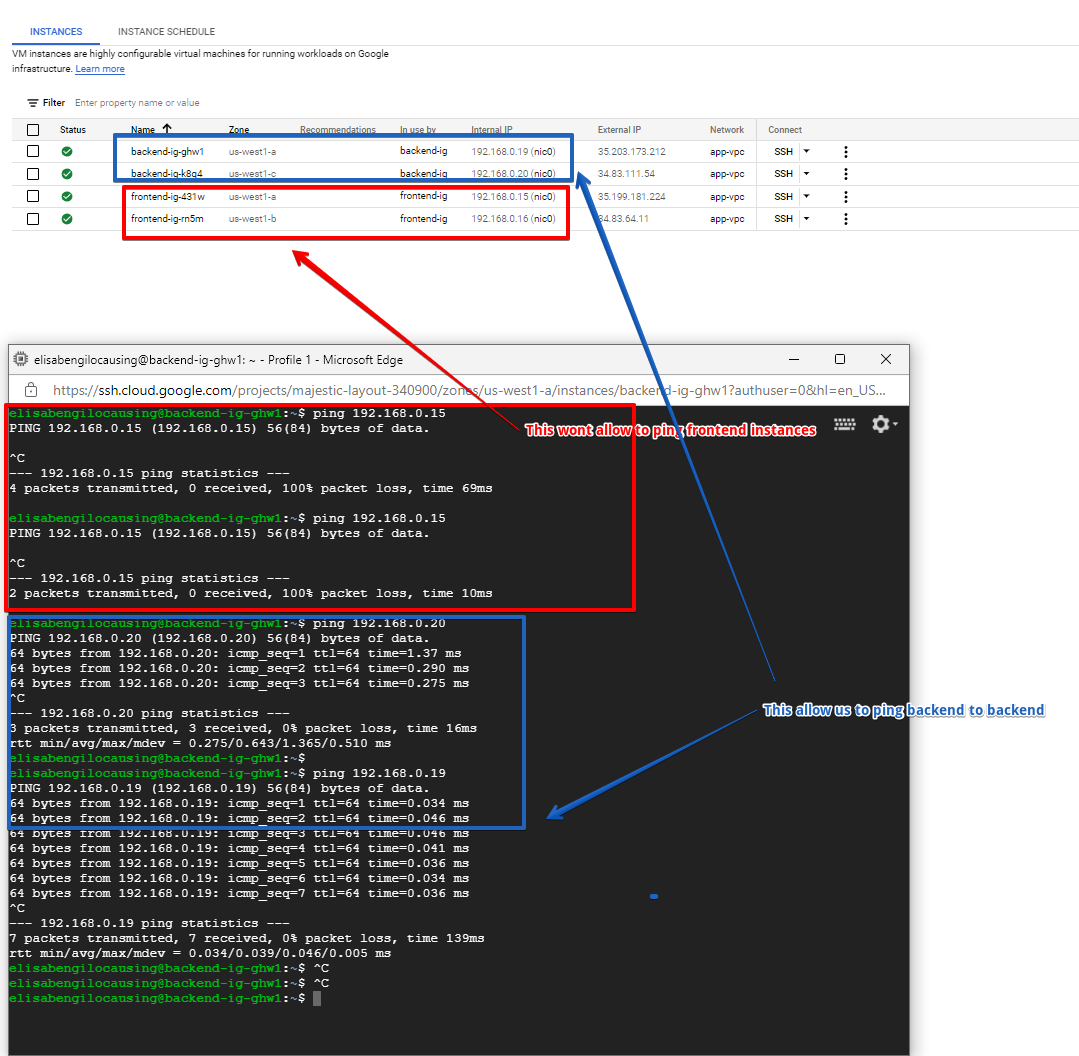
- When SSHed to frontend instances:
- Can ping backend instances (including cross-zones)
NOTE: You can ping only the internal IP address and not external address. That is because of this Tier setup:
Backend – Should NOT accept incoming request from the internet
So external IP is considered as the “Internet”

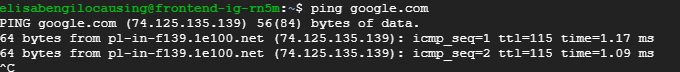
- When SSHed to frontend instances:
- Can ping google.com
- When SSHed to backend instances:
- Should not be able to ping frontend instances
- Can ping other backend instances
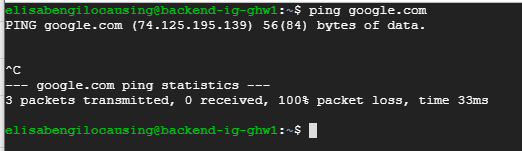
- When SSHed to backend instances:
- Should not be able to ping google.com
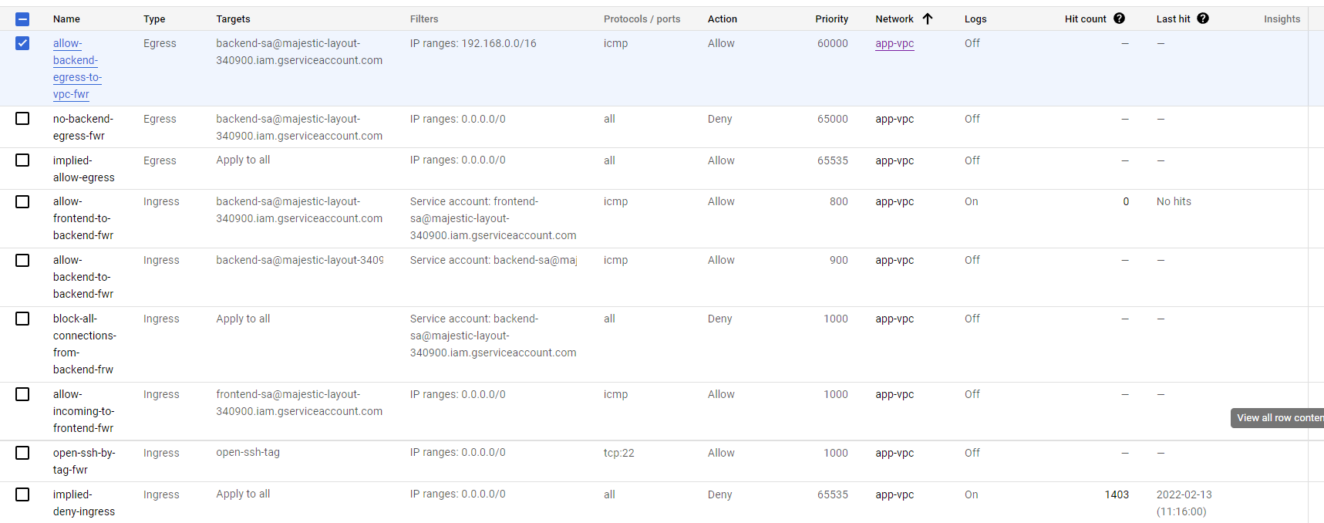
How it works?
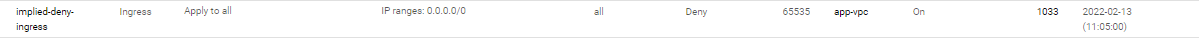
First, this blocks everything – all instances, etc.
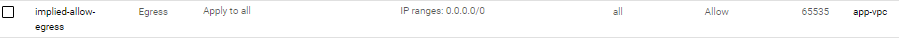
Second, then it allows all egress/outgoing – Which means it can ping, google, front-end and backend.
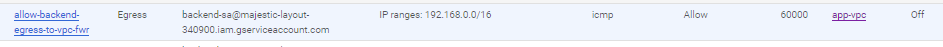
Third, all egress/outgoing from backend will be blocked. All backend instances only!

Fourth, all egress/outgoing targeting all backends will be allowed by the IP range of our VPC for ICMP protocol

Overall VPC Firewall Rules