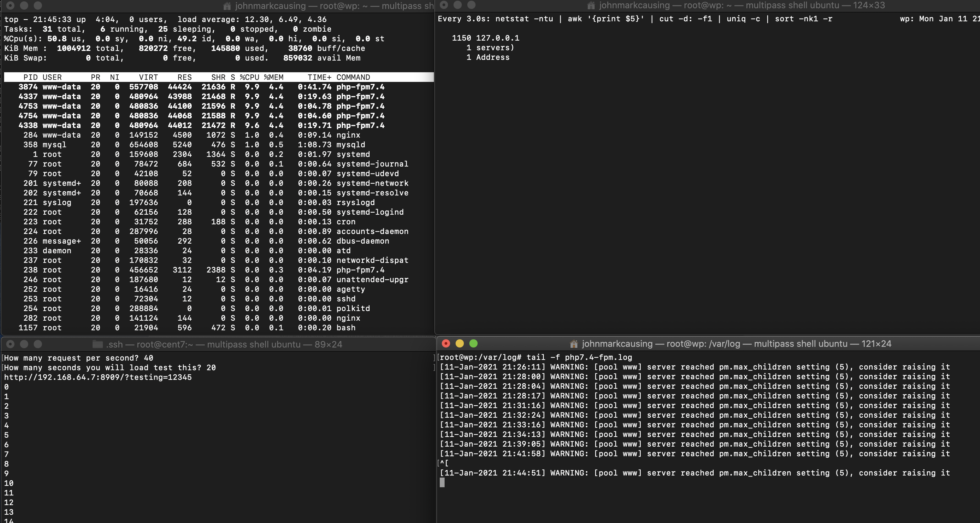
Testing a server with 1 CPU and 5 php workers. Using netstat command with watching every 3 seconds to capture the IP of the incoming connection.
Sending 30 php request per seconds (last 30 seconds)
Github source: https://github.com/jmcausing/linux-basic-scripts/blob/main/loadtest.sh
watch -n 3 "netstat -ntu | awk '{print $5}' | cut -d: -f1 | uniq -c | sort -n"Load test from localhost targeting Linode vps 1 CPU (shared)
Screenshot below shows 4 terminal windows. Top right shows 445 incoming connection from that IP address. Lower right shows that php workers reached their limits 4 times over. Lower left is the terminal from my local machine with the load test script.

Load test from localhost targeting localhost
Basic load testing script that uses random string url.
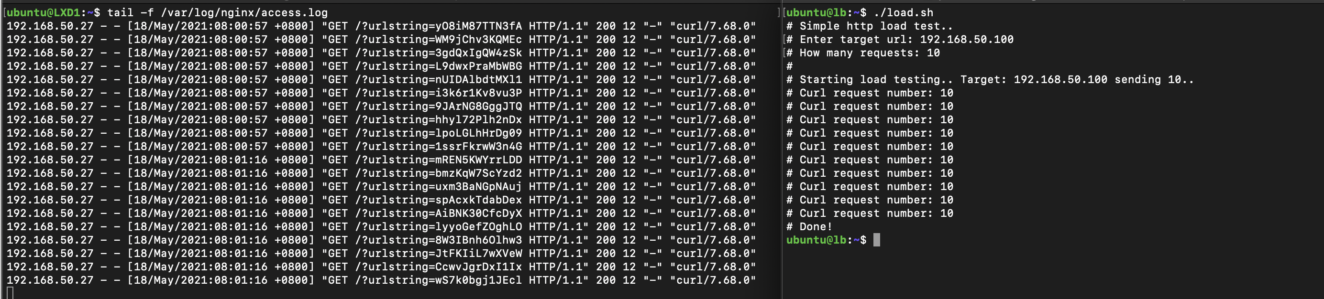
Code sample:
#!/bin/bash
echo "# Simple http load test.."
read -p "# Enter target url: " url
read -p "# How many requests: " nr
echo "#"
echo "# Starting load testing.. Target: $url sending $nr.. "
a=0
while [ $a -lt $nr ]
do
echo "# Curl request number: $nr"
randstring=$(tr -dc A-Za-z0-9 </dev/urandom | head -c 13 ; echo '')
curl $url?urlstring=$randstring &> /dev/null
a=$((a+1))
done
echo "# Done!"Identifying the attacker.
Screenshot below shows there are lots of incoming connection from that IP with the 443 port request.
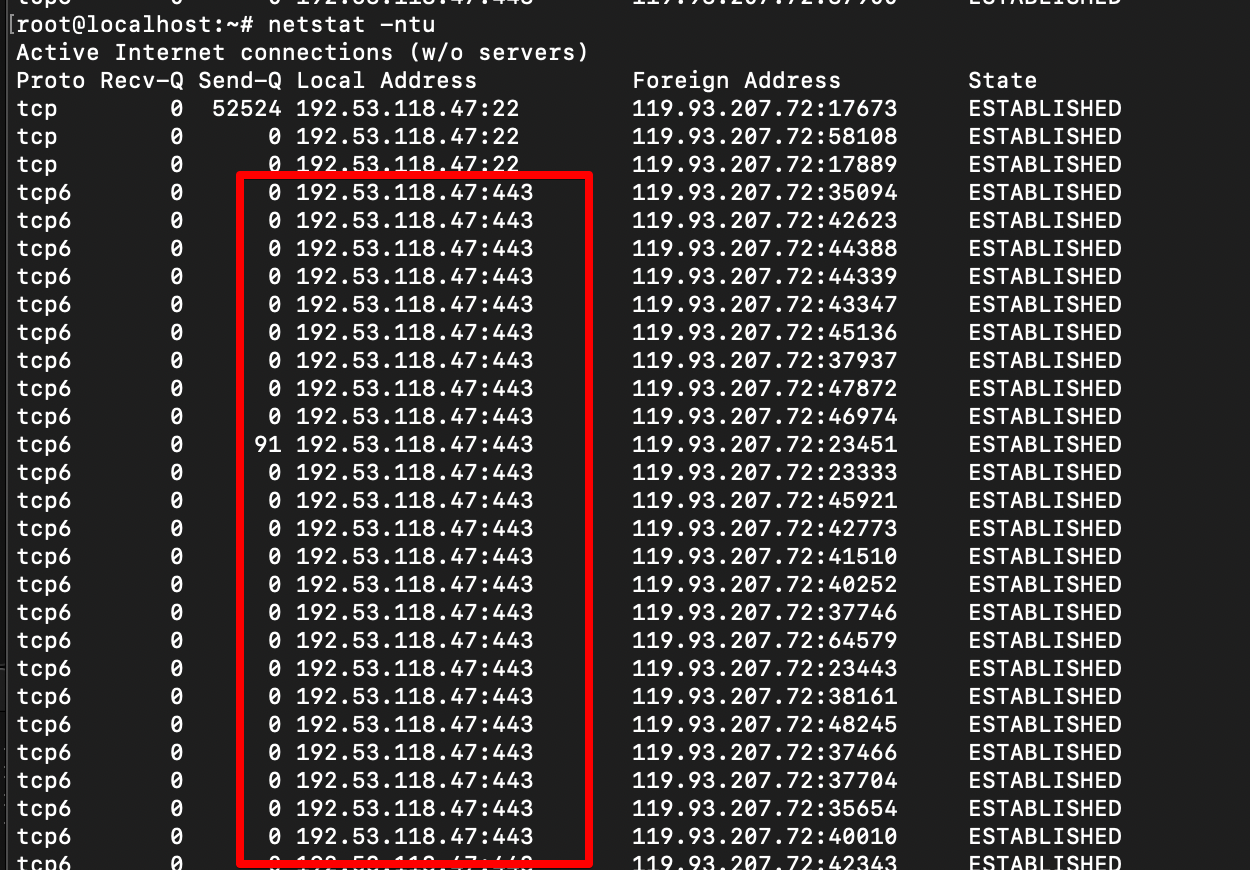
Using watch and netstat combination with awk, sort and uniq we can filter and count the incoming connection.
watch -n 2 "netstat -ntu | awk '{print $5}' | cut -d: -f1 | uniq -c | sort -n "
Now we know the IP of the attacker and the port that IP is trying to access, we can now block it using ip tables.
Before blocking that IP from IP tables
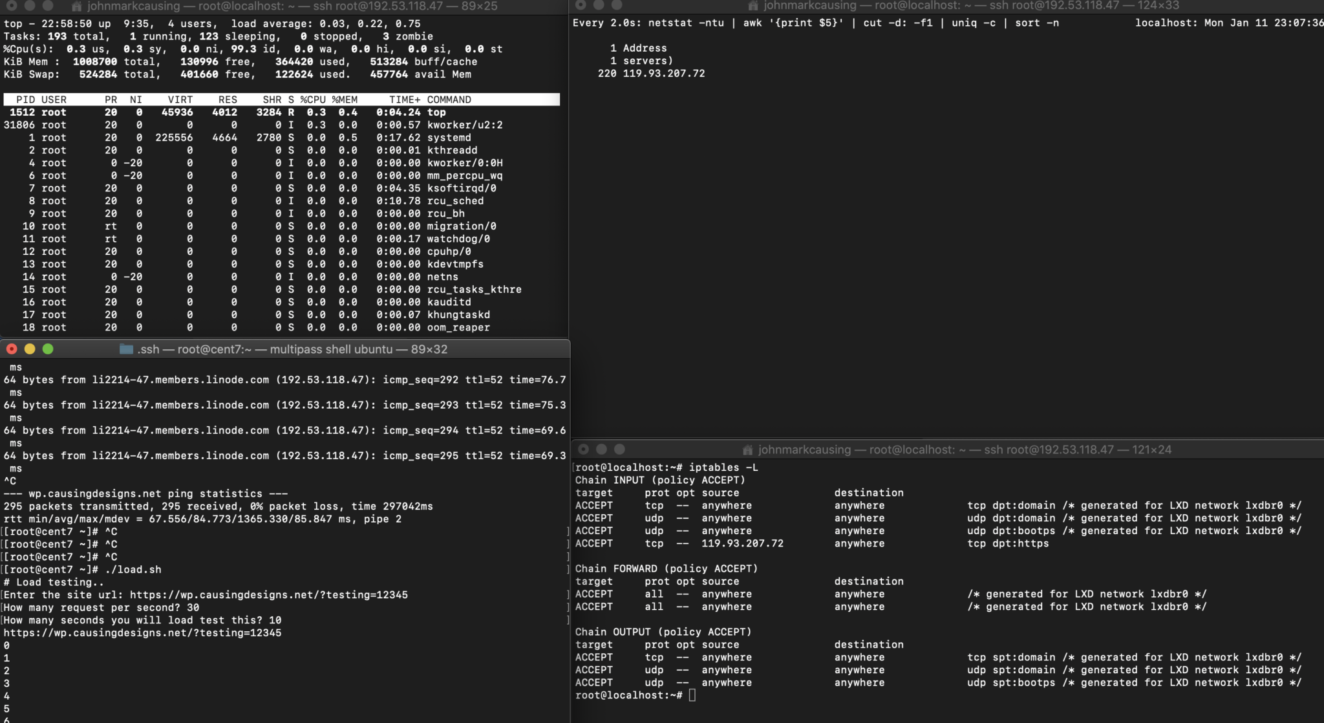
After blocking the IP on a specific port 443
